NCC Group: Ransomware attacks jump 73% in February
While NCC Group expected an increase in ransomware attacks from January to February, year-over-year data showed just how persistent the threat is to enterprises.
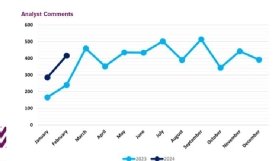
NCC Group anticipates 2024 ransomware activity will surpass last year's staggering levels based on record-setting numbers for January and February.
In January, NCC Group researchers determined the number of ransomware attacks increased by 73% compared to 2023, and February data followed the same pattern.
"Observed ransomware attacks have, as is to be expected, increased significantly from January 2024 to February 2024 from 285 to 416 cases, marking a 46% increase month on month which is once again the highest figure that we have witnessed in February (73% higher than February 2023)," NCC Group wrote in the report. "If 2024 is to follow the same pattern as 2023, we can expect a further increase going into March as we start to reach the baseline for 2024's ransomware activity, which will likely consistently surpass that of 2023 based on previous trends."
NCC Group added that "February was quite the standout month for ransomware" based on attack volume and a shift in threat actors activity level. While the LockBit 3.0 ransomware group maintained its top spot as NCC Group's most active actor for the seventh consecutive month, activity spiked for two newer groups.
Hunters International emerged onto the threat landscape in 2023, but affiliates used Hive ransomware code during attacks. In January, the Department of Justice announced the FBI disrupted Hive infrastructure and obtained decryption keys to help victim organizations recover. Since emerging in 2022, ransomware as a service (RaaS) group Qilin warranted a warning from cybersecurity vendor Group-IB, as operators targeted organizations in critical sectors.
Breaking down the numbers, NCC Group discovered that LockBit claimed responsibility for 110 attacks in February compared to 64 attacks in January. Though Hunters trailed right behind LockBit in the top 10 list, only 33 attacks were connected to the gang. NCC Group noted that Hunters made the top ten threat actor list previously, but February was the first time it made it to the top three.
NCC Group
Qilin tied with the infamous BlackCat/Alphv ransomware gang, which claimed responsibility for last month's disruptive attack against UnitedHealth's Change Healthcare, for the third most active threat actor in February with 30 attacks.
"Though BlackCat is accustomed to being included in the most active monthly threat groups, Qilin, like Hunters is relatively new to these levels of activity," the report read.
Josh Callicott-Oelmann, threat intelligence analyst at NCC Group, told TechTarget Editorial the firm first observed Hunters activity in November. However, NCC Group only recorded three attacks compared to 33 in February. He attributed Hunter's rise in activity to operators evolving and improving capabilities.
Callicott-Oelmann also addressed Hunter's connection to Hive.
"Although there has been speculation about the group being an offshoot of Hive, Hunters confirmed that they are an independent group that have acquired Hive's source code and infrastructure. Additionally, what is known is they tend to keep their targeting simple, following the common targeting of the industrials sector," Callicott-Oelmann told TechTarget Editorial.
LockBit down?
Last month's significant increase in ransomware activity occurred despite a joint international law enforcement effort to disrupt the most active group. On Feb. 20, the U.K.'s National Crime Agency announced it seized LockBit's infrastructure as part of a broader international law enforcement effort dubbed Operation Cronos. The takedown proved temporary when LockBit restored its servers within days.
Subsequently, LockBit deployed attacks against vulnerable ConnectWise customers by exploiting a critical ScreenConnect vulnerability that was disclosed in February. Reports, including one by cyber insurer Coalition, cited substantial differences between how the group operated before and after the FBI takedown, even though it was short lived. The change in tactics aligns with NCC Group's observations as well.
"However, once tarred with the brush of law enforcement intervention, it is hard for a cyber threat group to operate as before as they are, naturally, treated with suspicion by other players in the game," the report read.
The report emphasized that since LockBit is such a big player, any action around the group will influence the landscape. Moving forward, NCC Group said it's possible that LockBit affiliates might switch to other RaaS gangs to distance themselves in anticipation of law enforcement's next move against the group.
For example, when the Conti ransomware group disbanded in 2022, cybersecurity vendors confirmed that operators rebranded as other gangs, such as the Black Basta ransomware group.
Callicott-Oelmann confirmed LockBit has resumed operations after Operation Cronos with new infrastructure, encryptors and websites.
"They also managed to maintain access to their victims' stolen data and even included the FBI on their data leak site, according to our data. Since their resurgence, we have seen ransomware attacks continue from the group, with 20 observed so far in March," Callicott-Olemann said.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.
Source https://www.techtarget.com/searchsecurity/news/366574878/NCC-Group-Ransomware-attacks-jump-73-in-February